|
||||
| ||||
Microsoft Office email SPOOF
This is a warning about an apparent PHISHING attempt to get information or possible malware infection attempt by spoofing a Microsoft Office email.
This example shows how well crafted a spoof email can be. At first glance the original email looked convincingly like an actual Microsoft Office email - but it is not.
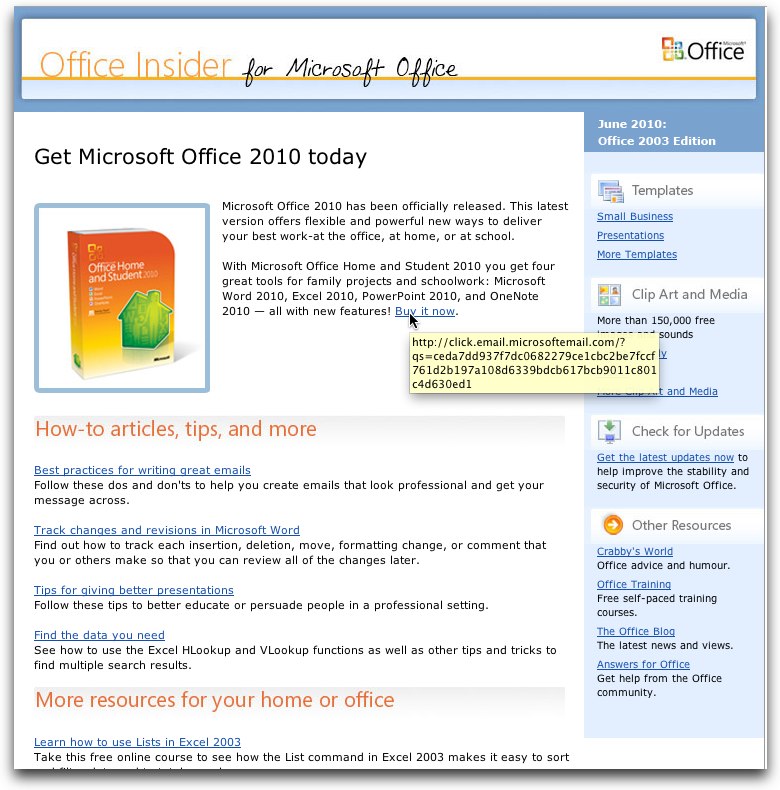
Shown below is a JPEG screenshot of the subject email. We have used the screenshot image what the actual email looks like without having the danger of passing any live links.
NOTE that this email was NOT from Microsoft at all! it is crafted to LOOK like it came from Microsoft, but in fact has nothing at all to do with Microsoft. The creator of the original email has 'spoofed' a Microsoft Office email in an attempt to get the viewer's trust and click on one (or more) links in the original email ostensibly for the purpose of "phishing".
("Phishing" is an attempt to gain information of some sort from the potential victim that is viewing the spoofed email.)
Here is the 'giveaway' - how to tell it is not really a Microsoft Office email
Using the technique of "hovering", the actual underlying link is revealed and we can see that it is NOT actually a real Microsoft URL (address).
("Hovering" is the technique of moving the mouse over a link in the email (or on a web page) and waiting a second or two; a block should appear showing the actual underlying link.)
In the below attached example, we have captured the screenshot while hovering over the "Buy it now" link in the original email. Note that hovering on ALL the links in the original email produced a similar effect.
Note that the link shown in the resultant 'hover' block in the below attachment shows the URL "Xclick.email.microsoftemail.comX" - which is NOT a Microsoft URL - followed by a question mark, which is in turn followed by a series of alphanumeric characters. (NOTE that we have preceded and appended an "X" to the actual URL to effectively disable the link and prevent any reader of this from accidentally clicking on and following the actual link.)
Suffice to say, this is an obvious spoof and is most likely designed to gain some sort of information - or possibly pass a virus or other malware back to anyone following (clicking on) any of the links in the original email.
This example shows how elaborate and well crafted some spoofs can be. As you can see from the below screenshot of the spoof email, it is quite a good job and really does look very much like a real Microsoft Office email. So much so, in fact, that it would not be surprising to learn a number of people receiving such a spoof could easily fall prey to it and actually click on one or more links.
Additional information
non-essential supplemental information for the 'curious' reader
When a URL link is followed by a question mark in HTML (either email or webpage) as in this case, the information following the question mark is passed to the linked webpage. Such information can be your email address or some other information, possibly coded (as in this example) whereby the perpetrator will obtain some information regarding from where (or from whom) the link was followed.
In this case the shown URL is actually a sub-domain ("click") of a sub-domain "email" of the domain "Xmicrosoftemail.comX". The domain itself is chosen to be something that LOOKS like "microsoft" in the apparent hope that the intended victim will THINK it actually IS Microsoft and put them off their guard.
We did some further investigation and found that the linked webpage in the original email goes to an ASP (Active Server Page) webpage entitled "AOL Page". We do NOT recommend anyone try to follow the original link. An ASP has the capability of running ACTIVE content on the viewer's computer; such content could possibly be some sort of detrimental malware.
| Support Area |
All graphics, logos, advertisements and
promotions are Copyright ©DayComSolutions.com 2005-2012 All Rights Reserved |
